Computer Security:-
Computer Security is the process of detecting and preventing any unauthorized use of your laptop/computer. It involves the process of safeguarding against trespassers from using your personal or office based computer resources with malicious intent or for their own gains, or even for gaining any access to them accidentally.
Why Security?
Cyberspace (internet, work environment, intranet) is becoming a dangerous place for all organizations and individuals to protect their sensitive data or reputation. This is because of the numerous people and machines accessing it. It is important to mention that the recent studies have shown a big danger is coming from internal threats or from disappointed employees like the Edward Snowden case, another internal threat is that information material can be easy accessible over the intranet.
One important indicator is the IT skills of a person that wants to hack or to breach your security has decreased but the success rate of it has increased, this is because of three main factors
Cyberspace (internet, work environment, intranet) is becoming a dangerous place for all organizations and individuals to protect their sensitive data or reputation. This is because of the numerous people and machines accessing it. It is important to mention that the recent studies have shown a big danger is coming from internal threats or from disappointed employees like the Edward Snowden case, another internal threat is that information material can be easy accessible over the intranet.
One important indicator is the IT skills of a person that wants to hack or to breach your security has decreased but the success rate of it has increased, this is because of three main factors
- Hacking tools that can be found very easily by everyone just by googling and they are endless.
- Technology with the end-users has increased rapidly within these years, like internet bandwidth and computer processing speeds.
- Access to hacking information manuals.
All this can make even a school boy with the curiosity, a potential hacker for your organization.




Since locking down all networks is not an available option, the only response the security managers can give is to harden their networks, applications and operating systems to a reasonable level of safety, and conducting a business disaster recovery plan.
What to Secure?
Let’s see this case, you are an IT administrator in a small company having two small servers staying in a corner and you are very good at your job. You are doing updates regularly, setting up firewalls, antiviruses, etc. One day, you see that the organization employees are not accessing the systems anymore. When you go and check, you see the cleaning lady doing her job and by mistake, she had removed the power cable and unplugged the server.
What I mean by this case is that even physical security is important in computer security, as most of us think it is the last thing to take care of.
Now let’s go directly to the point of what all to secure in a computer environment −
- First of all, is to check the physical security by setting control systems like motion alarms, door accessing systems, humidity sensors, temperature sensors. All these components decrease the possibility of a computer to be stolen or damaged by humans and environment itself.
- People having access to computer systems should have their own user id with password protection.
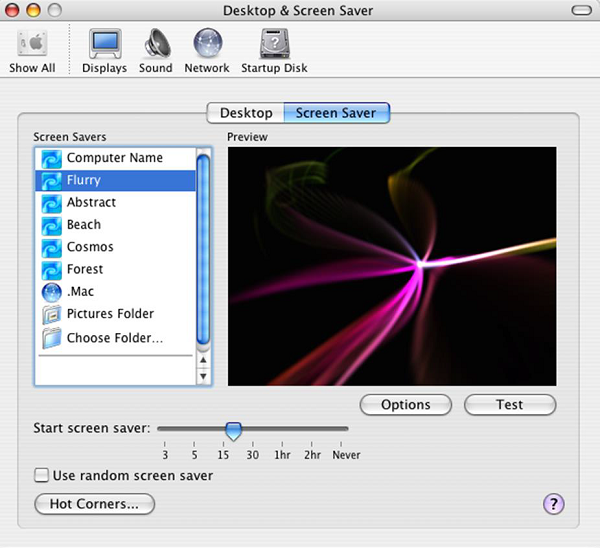
- Monitors should be screen saver protected to hide the information from being displayed when the user is away or inactive.
- Secure your network especially wireless, passwords should be used.
- Internet equipment as routers to be protected with password.
- Data that you use to store information which can be financial, or non-financial by encryption.
- Information should be protected in all types of its representation in transmission by encrypting it.
Potential Losses due to Security Attacks:-
The potential loses in this cyberspace are many even if you are using a single computer in your room. Here, I will be listing some examples that have a direct impact on you and on others −
- Losing you data − If your computer has been hacked or infected, there is a big chance that all your stored data might be taken by the attacker.
- Bad usage of your computer resources − This means that your network or computer can go in overload so you cannot access your genuine services or in a worst case scenario, it can be used by the hacker to attack another machine or network.
- Reputation loss − Just think if your Facebook account or business email has been owned by a social engineering attack and it sends fake information to your friends, business partners. You will need time to gain back your reputation.
- Identity theft − This is a case where your identity is stolen (photo, name surname, address, and credit card) and can be used for a crime like making false identity documents.
-
Basic Computer Security Checklist
- There are some basic things that everyone of us in every operating system need to do −
- Check if the user is password protected.
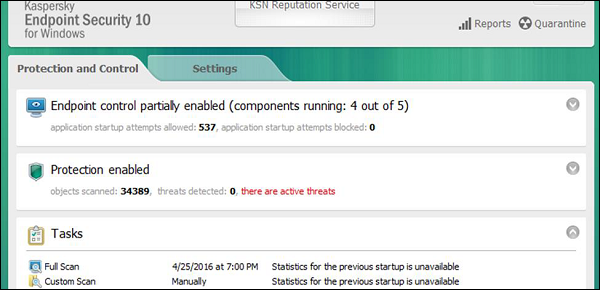
- Check if the operating system is being updated. In my case, I did a screenshot of my laptop which is a Windows 7.
- Check if the antivirus or antimalware is installed and updated. In my case, I have a Kaspersky antivirus being updated.
- Check for the unusual services running that consumes resources.
- Check if your monitor is using a screen saver.
- Check if the computer firewall is on or not.
- Check if you are doing backups regularly.
- Check if there are shares that are not useful.
- Check if your account has full rights or is restricted.
- Update other third party software’s
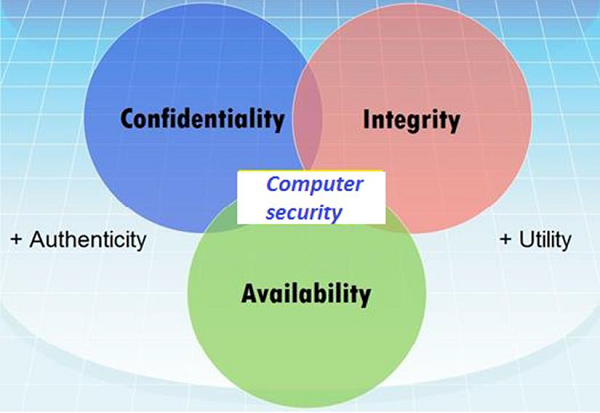
Computer Security-Elements:-
The general state in Computer Security has the ability to detect and prevent attacks and to be able to recover. If these attacks are successful as such then it has to contain the disruption of information and services and check if they are kept low or tolerable.
Different Elements in Computer Security
In order to fulfil these requirements, we come to the three main elements which are confidentiality, integrity, and availability and the recently added authenticity and utility.

Confidentiality
Confidentiality is the concealment of information or resources. Also, there is a need to keep information secret from other third parties that want to have access to it, so just the right people can access it.
Example in real life − Let’s say there are two people communicating via an encrypted email they know the decryption keys of each other and they read the email by entering these keys into the email program. If someone else can read these decryption keys when they are entered into the program, then the confidentiality of that email is compromised.

Integrity
Integrity is the trustworthiness of data in the systems or resources by the point of view of preventing unauthorized and improper changes. Generally, Integrity is composed of two sub-elements – data-integrity, which it has to do with the content of the data and authentication which has to do with the origin of the data as such information has values only if it is correct.
Example in real life − Let’s say you are doing an online payment of 5 USD, but your information is tampered without your knowledge in a way by sending to the seller 500 USD, this would cost you too much.
In this case cryptography plays a very major role in ensuring data integrity. Commonly used methods to protect data integrity includes hashing the data you receive and comparing it with the hash of the original message. However, this means that the hash of the original data must be provided in a secure way.
Availability
Availability refers to the ability to access data of a resource when it is needed, as such the information has value only if the authorized people can access at right time. Denying access to data nowadays has become a common attack. Imagine a downtime of a live server how costly it can be.
Example in real life − Let’s say a hacker has compromised a web server of a bank and put it down. You as an authenticated user want to do an e-banking transfer but it is impossible to access it, the undone transfer is a money lost for the bank.
Computer Security-Terminologies:-
- Unauthorized access − An unauthorized access is when someone gains access to a server, website, or other sensitive data using someone else's account details.
- Hacker − Is a Person who tries and exploits a computer system for a reason which can be money, a social cause, fun etc.
- Threat − Is an action or event that might compromise the security.
- Vulnerability − It is a weakness, a design problem or implementation error in a system that can lead to an unexpected and undesirable event regarding security system.
- Attack − Is an assault on the system security that is delivered by a person or a machine to a system. It violates security.
- Antivirus or Antimalware − Is a software that operates on different OS which is used to prevent from malicious software.
- Social Engineering − Is a technique that a hacker uses to stole data by a person for different for purposes by psychological manipulation combined with social scenes.
- Virus − It is a malicious software that installs on your computer without your consent for a bad purpose.
- Firewall − It is a software or hardware which is used to filter network traffic based on rules.
Computer Security-OS Security:-
Guidelines for Windows OS Security
Following are the list of guidelines for Windows Operating System Security.
Use the licensed versions of Windows OS, not the cracked or pirated ones and activate them in order to take genuine updates.

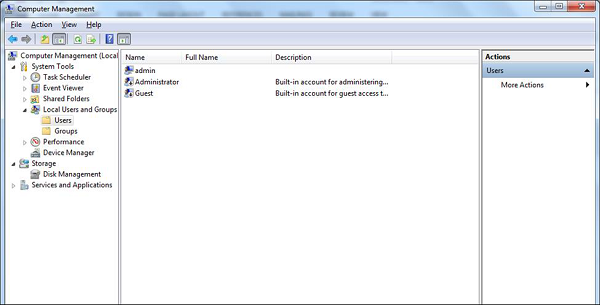
Disable Unused Users − To do this, Right Click on Computer – Manage – Local Users and Groups – Users, then disable those users that are not required. In my case, I disabled the Guest and Administrator users and I created a new non-default like Admin.

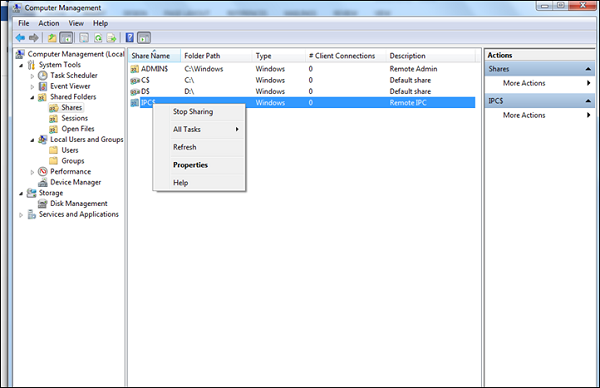
Disable unused shares − By default, Windows OS creates shares, please see the following screenshot. You have to disable them and to do this, you follow −
Right Click on My Computer – Manage – Shared Folders – Right Click Stop Sharing.

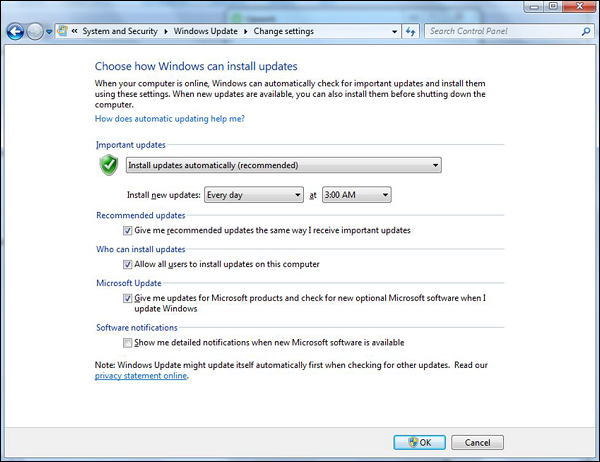
The next step is to take updates regularly for Windows OS. It is reccomended to do them automatically and periodically. To set this up, go to Control Panel – System and Security – Windows Updates – OK.

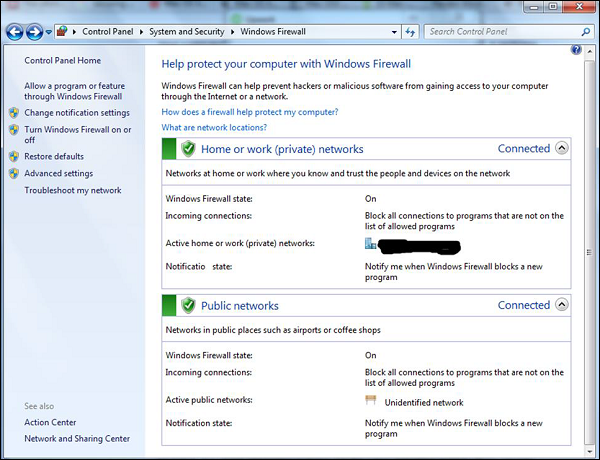
Put your Windows System Firewall up, this will block all the unauthorized services that make traffic. To set this up, go to Control Panel – System and Security – Windows Firewall.

Install a licensed antivirus and take updates, in the coming sections we will cover in detail about antiviruses. It is strongly recommended not to download from torrents and install cracked versions.

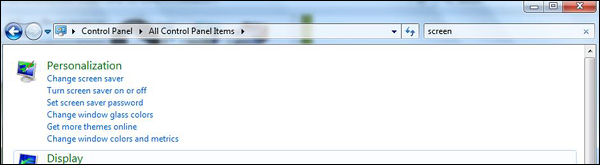
You should always Configure a password protected Screen Saver. To set this up, please follow this path −
Control Panel – All Control Panel Items – Personalize – Turn Screen Saver on or off – Check “On resume, display logon Screen”.

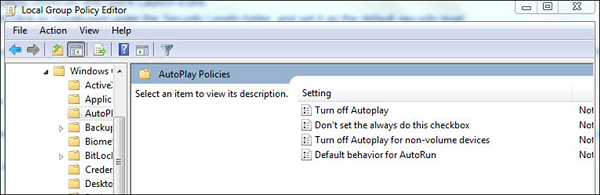
Disable Autoplay for Removable Media. This blocks the viruses to run automatically from removable devices.
To disable it go to – Start – on Search box type Edit Group Policy –Administrative Templates – Windows Components – Autoplay Policy – Turn off Autoplay – Enable – Ok.

Install only trusted internet explorer browsers like Internet explorer, Chrome or Mozilla Firefox and then update them regularly. Missing the updates can lead to possible hacking.
Guidelines for Mac OS X Security
Following are the list of guidelines for Mac OS X Security.
Use licensed versions of Mac OS X and never use the cracked or pirated ones. Once installed, activate them in order to take up the genuine updates.

Set password for the root user and create a less privileged user. By default, the root user of the Mac OS X doesn’t have a password, so you have to put one and then create a user with less privilege for daily usage.
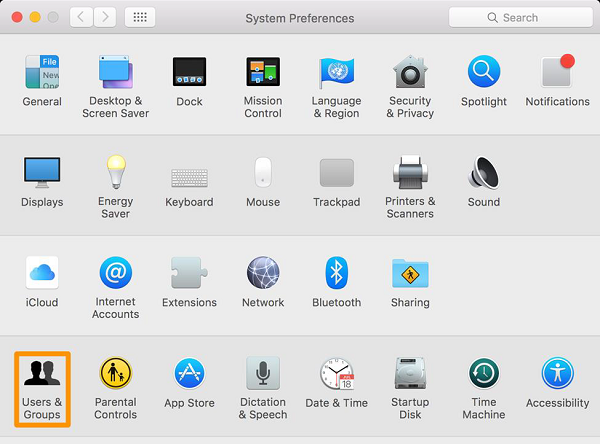
To set it up follow: Apple menu – System Preferences – Click Users & Groups

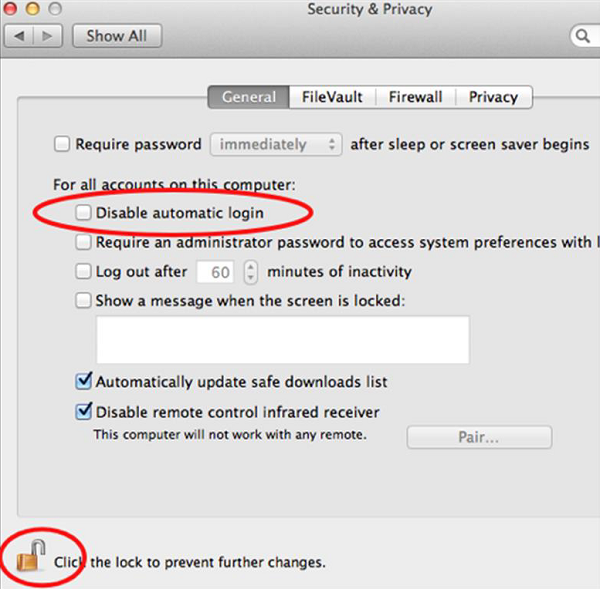
Disable Auto Logon − By default, the Mac OS X is configured to automatically logon the first administrative user that is created. Also it displays all valid usernames in the login windows.
To disable this, you have to: Open System Preferences – Accounts – User – Uncheck the Log in automatically – Click on Login Options (tab) – Set “Display Login Windows as” = Name and Password.

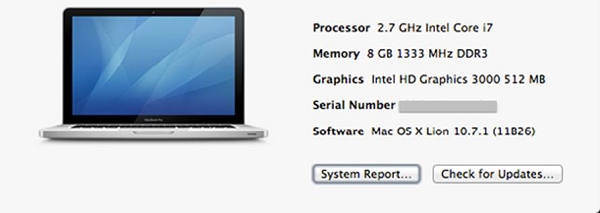
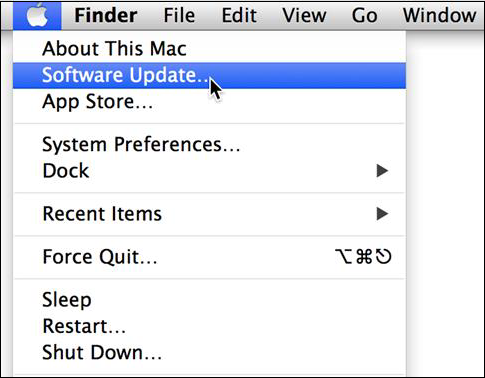
Update Mac OS X − In order to secure our systems, we need to take our updates and patches of Mac OS X.
To do so we follow this path: Click on System Preferences –Software Update – Change the default “weekly” to “daily” – Quit System Preferences.
You better do it weekly because it will not overload your networks, in case you have a large network.

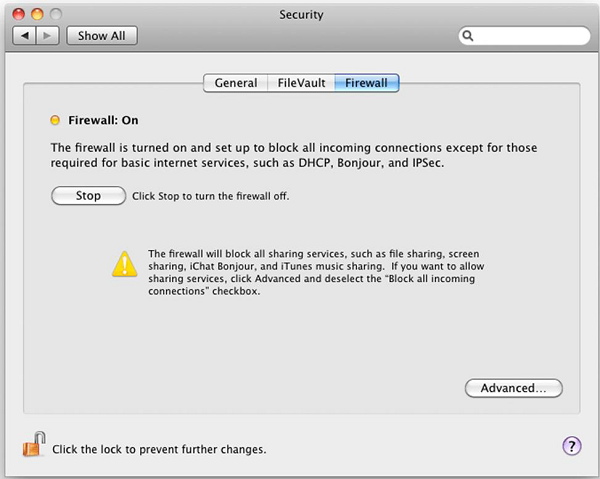
Put your Mac OS X system firewall up. The go to System Preferences – Sharing –Firewall – Click on Start.

Configure Screen saver password protected: To set this up, follow this path – System Preferences – Screen Effect – Activation – Set “Time until screen effect starts” = 5 Minutes – Set “Password to use when waking the screen effect” = use my user –account password. It is recommended to be less than 5 minutes.

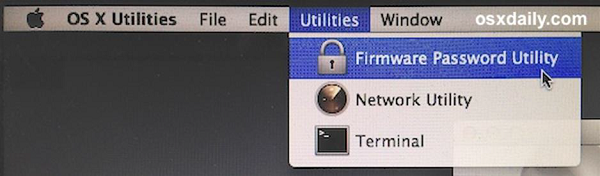
Put Open Firmware password − Double click the application icon to open it. Click on the "Change" button to modify the security settings. If you are enabling the security features, enter a password into the – Password and Verify boxes. Click OK. Enter your System Administrator Account.

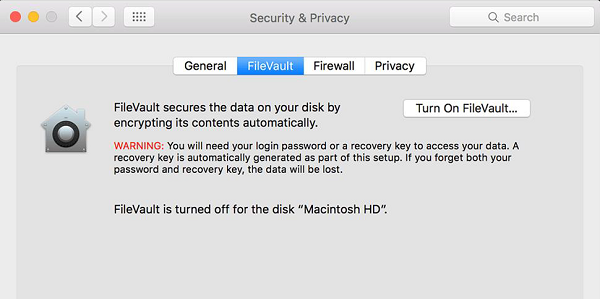
Encrypt folders − Mac OS X has FileVault, which encrypts information in your home folder. You can see the FileVault in the following screenshot.
Click Apple Menu – System Preferences – Security & Privacy – FileVault – Click the lock Icon to unlock it, then enter an administrator name and password.
Then you will have to Turn On FileVault.

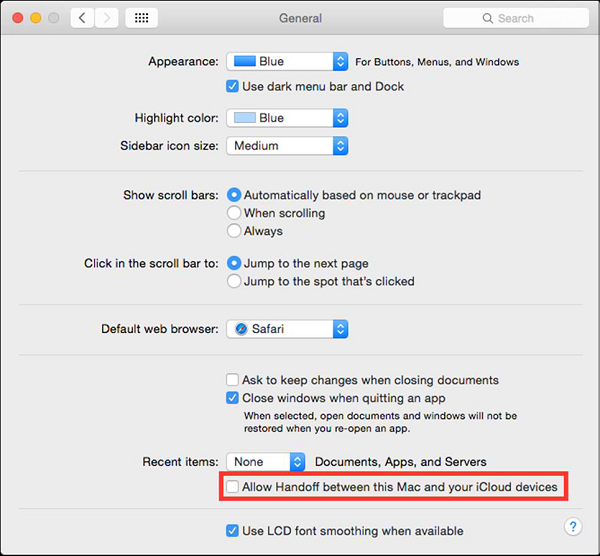
Disable Handoff − Handoff is a feature to keep your work in sync, but it needs to send some data to Apple to work. It is suggested to disable it.
To do so: Click System Preferences – General – Uncheck “Allow Handoff between this Mac and your iCloud devices”.

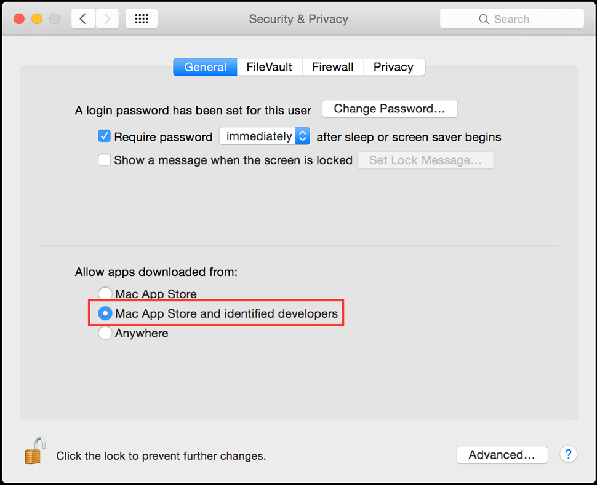
Allow only signed Apps − To reduce the surface of attack, it is suggested not to run untrusted code not signed with a proper key.
To allow only apps signed by an authorized developer, you should follow the path – System Preferences – Security & Privacy –General – Set “Allow apps download from” to “Mac App Store and identified developers”.

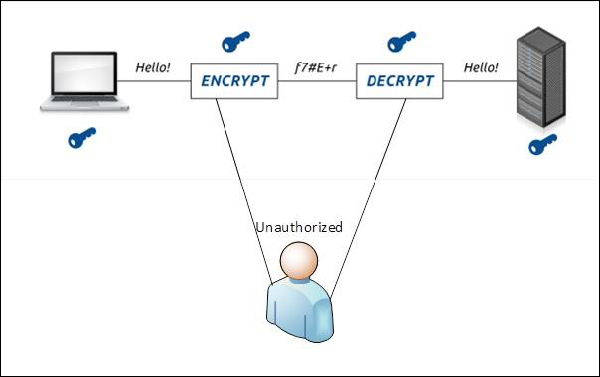
Computer Security-Encryption:-
What is Encryption?
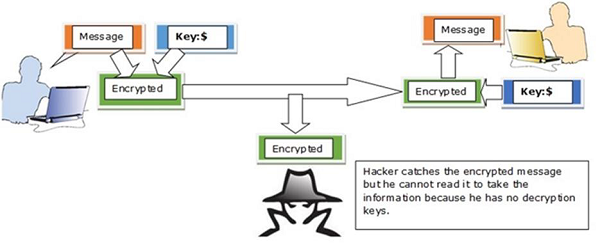
Encryption is a transformed type of genuine information where only the authorized parties know how to read it, so in the worst case scenario if somebody has access to these files they would still not be able to understand the message in it.
The bases of encryption are since the ancient times. A good example is the pigeon couriers, where the kings used to send messages to their commandants in the battle field in a specific code, when the enemies caught them, they could not read them, just that the message was lost, but if arrived at the destination commandant had the decryption vocabulary so they could decrypt it.

We should mention that encryption is for good or bad purpose. The bad case is the scenario in which most of the malware files are in an encrypted form, so it cannot be read by everyone accept the hacker.
Tools Used to Encrypt Documents
In this tutorial we will focus more on the practices than on the theoretical aspects for better understanding. Let us discuss about some tools that we use to encrypt documents −
- Axcrypt − It is one of the best opensource encryption file softwares. It can be used in Windows OS, Mac OS and Linux as well. This software can be downloaded from − http://www.axantum.com/AxCrypt/Downloads.aspx
- GnuPG − This is an opensource software again and it can be integrated with other softwares too (like email). It can be downloaded from − https://www.gnupg.org/download/index.html
- Windows BitLocker − It is a Windows integrated tool and its main functions is to secure and encrypt all the hard disk volumes.
- FileVault − It is a Mac OS integrated tool and it secures as well as encrypts all the hard disk volume.
Encryption Ways of Communication
System Administrators should use and offer to their staff a secure and encrypted channels of communication and one of them is SSL (Secure Sockets Layer).This protocol helps to establish a secure and encrypted connection between the clients and the servers. Generally, it is used for Web Servers, Mail Servers, FTP servers.
Why do you need this?
If you have an online shop and your clients are using their credit card and their personal data to purchase products from it. But they (Data) are at the risk to be stolen by a simple wiretapping as the communication is in clear text, to prevent this, SSL Protocol will help to encrypt this communication.
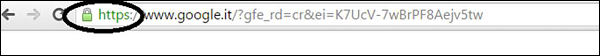
How to see if the communication is secure?
Browsers give visual cues, such as a lock icon or a green bar, to help visitors know when their connection is secured. An example is shown in the following screenshot.

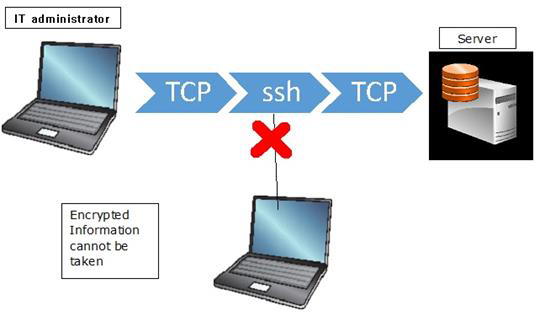
Another tool used by the system administrator is the SSH (Secure Shell). This is a secure replacement for the telnet and other unencrypted utilities like rlogin, rcp, rsh.
It provides a secure channel encrypted in the communication host to host over internet. It reduces the man-in-the-middle attacks. It can be downloaded from − http://www.putty.org/

Computer Security-Data Backup:-
Why is Backup Needed?
The main purpose is to recover the lost data from an unpredictable event like deletion by mistake or file corruption which in many cases is caused by a virus. An example is Ransomware, which encrypts all your data when your computer gets infected and the second is to roll back the data at a specific time you want. This is a scenario that happens often in companies which have applications and databases and they want to test their applications with a specific version of data.
How is this Process Managed at Big Companies?
It is suggested that in bigger companies which have a large volume of data, it is necessary to have a backup administrator, which is one of the most trusted persons in the company because he has access to all the data of that organization and generally deals with the backup routine check and the health of the backup.
Backup Devices
In this section we will see the backup devices from smaller to enterprise solutions. For a personal computer, they are −
CD and DVD, Blue-Rays − They are used for home/personal usage where people can store their documents, mainly personal or office related documents because they have small capacities varying from 750MB to 50GB.

Removable Devices − They are again for home usage (data, documents, music, photos, movies) which can be a Removable USB or external hard disks. Their capacities lately have increased a lot, they vary from 2 GB to 2 TB.

Network attached storage (NAS) − They are generally devices that are used in small businesses for backup purposes because they offer a centralized manner of backup. All the users can connect through the network to access this device and save data.
They are lesser in cost when compared to other solutions and they also offer a good fault tolerance as they are configured in RAID (redundant array of independent disks). They can be rack or non-rack mounted. They offer a good level of authentication of users and web console managing.

Storage Area Network (SAN) − These are generally devices that are used for big businesses for backup purposes. They offer a high speed of network for storage the biggest producers are EMC Corporation, DELL.

Types of Backups Based on Location
The types of backup can vary on the size of the business, budget and the data importance.
They are divided in two types −
- Local Backups
- Online Backups
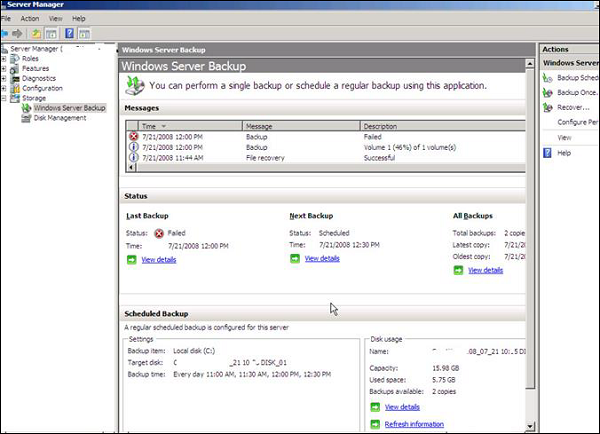
Generally local backups store the data in a CD, NA Storages, etc. as there can be a simple copying of files or by using any third party software. One of them in the server is the Windows backup which is included in the Windows Server Edition License.

Another one is Acronis which is one of the best in the market − http://www.acronis.com/en-eu/
Online Backup or Cloud Storage
One of the biggest trend is online storage where the companies and users can store their data somewhere in the cloud, and it is cheaper as well rather than doing it all by yourself. There is also no need for any backup infrastructure and maintenance.
For a personal user it is offered for free by the biggest vendors like Microsoft. It offers OneDrive and you can store up to 5GB in their cloud and it has an interface for different Operating Systems.
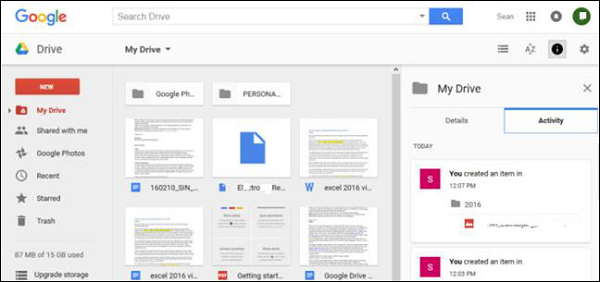
The second is the Google Drive, which is a product by google, wherein the files synchronizes automatically.

The full list can be seen in PCMagazine − http://www.pcmag.com/article2/0,2817,2413556,00.asp#. For small or big companies, mentioned before, online or cloud backup solution are a good solution for them because of the cost and the liability.
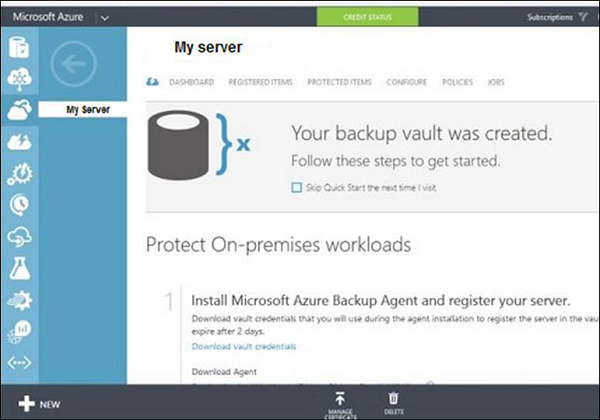
The biggest vendors offering such service are Microsoft with AZURE solution − https://azure.microsoft.com/en-us/documentation/scenarios/storage-backup-recovery/ which is offering a very high performance and scalability for this solution.

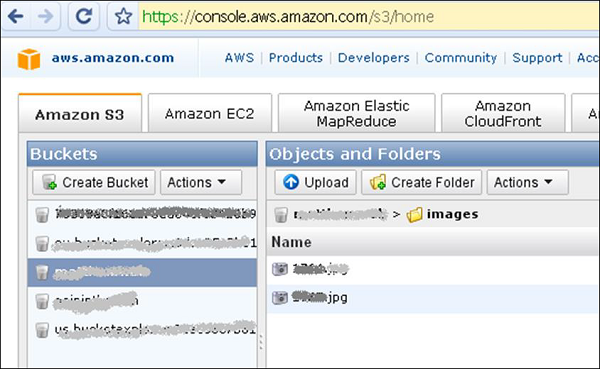
The other is Amazon with it product S3 details about this product can be found on − http://aws.amazon.com/s3/




No comments